Access Control List Implementation - Cisco Packet Tracer Lab
Overview:
This project demonstrates the configuration and application of a basic standard Access Control List (ACL) in a Cisco network environment using Packet Tracer. The goal was to control device access to a router by permitting specific IP addresses and blocking unauthorized devices.
Objectives:
- Allow PC0 (192.168.1.10) and PC1 (192.168.1.20) to access the router.
- Block PC2 from accessing the router.
- Demonstrate understanding of ACL creation, wildcard mask usage, and interface application.
Lab Topology:
- Router connected to a Switch.
- Three PCs (PC0, PC1, PC2) connected to the switch.
- All devices are configured within the 192.168.1.0/24 network.

Configuration Steps:
1. Access Privileged EXEC Mode:
Entered privileged mode using the "enable" command.
2. Enter Global Configuration Mode:
Accessed global configuration using configure terminal.
3. Create the Access Control List:
Defined ACL 10 to permit traffic only from the authorized IP addresses.
Bash:
"access-list 10 permit 192.168.1.10 0.0.0.0"
"access-list 10 permit 192.168.1.20 0.0.0.0"
Note: A wildcard mask of 0.0.0.0 was used to require an exact match of the source IP address.
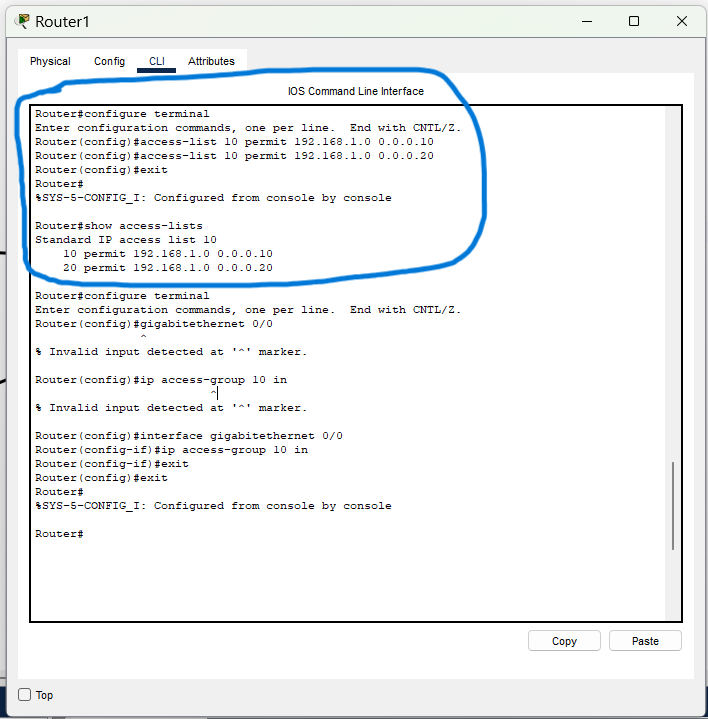
4. Apply the ACL to the Interface:
Applied ACL 10 to the LAN-facing router interface in the inbound direction.
Bash:
"interface GigabitEthernet0/0"
"ip access-group 10 in"
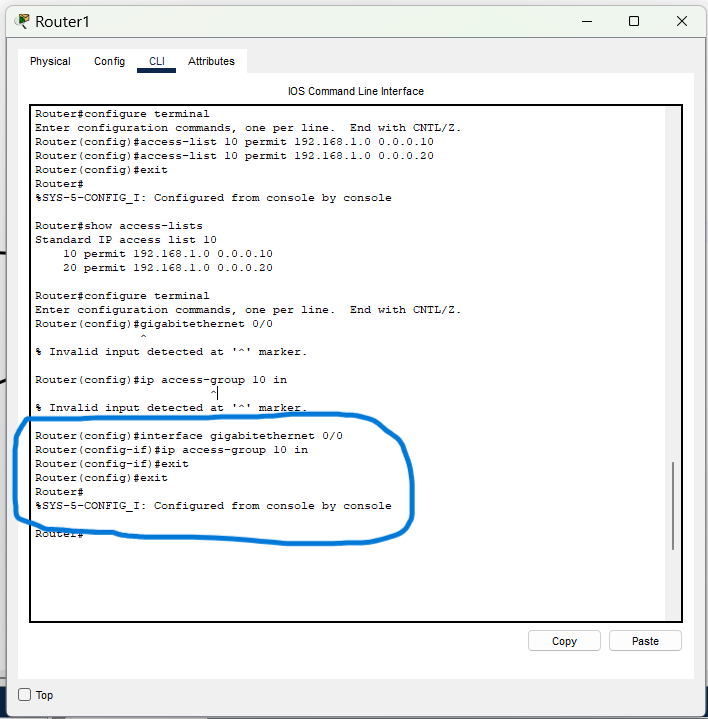
5. Verify Configuration:
Used show access-lists to confirm ACL rules were in place.
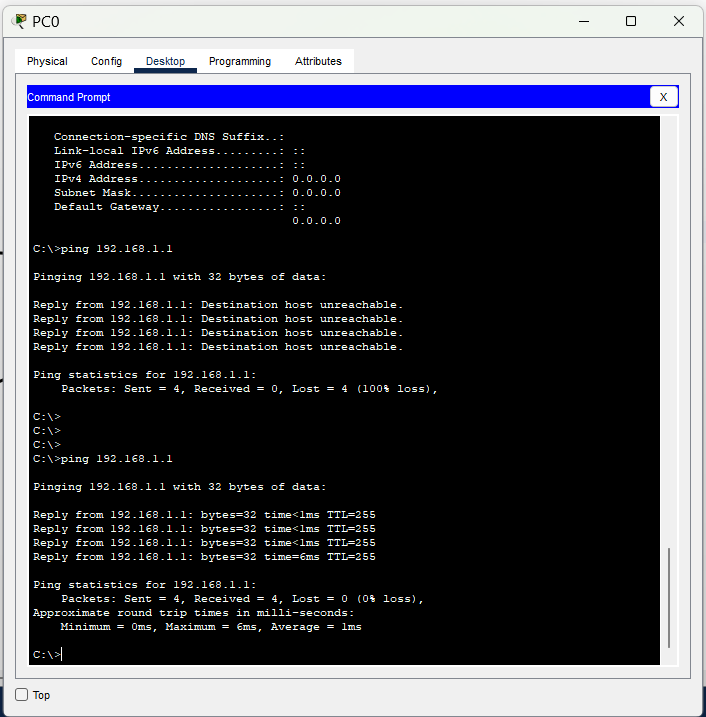
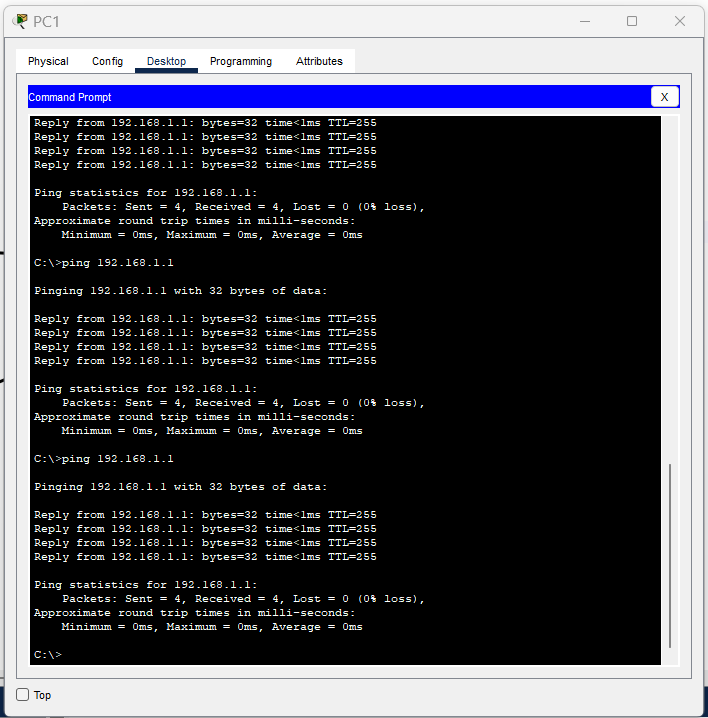
Tested connectivity by pinging the router from each PC:
PC0 and PC1 successfully pinged the router.
PC2 was correctly denied access.
Key Skills Demonstrated:
* Creation and application of standard ACLs
* Understanding of wildcard masks (0 = match exactly)
* Traffic filtering based on source IP
* Basic router and interface configuration
* Network security principles: least privilege and access control
Reflection:
This project reinforced key concepts of network access control, particularly how ACLs enforce network security by restricting access at the device level. It also highlighted the importance of precise wildcard masking and careful ACL planning to avoid unintended permissions.